Server Message Block (SMB)
It is a network communication protocol for providing shared access to files, printers,named pipe (Pipes are a way of streaming data between applications) and serial ports between nodes on a network (LAN).It uses Application Layer. It is the most exploited service , recent one -EternalBlue exploit used in wannacry ransomware attack (2017).
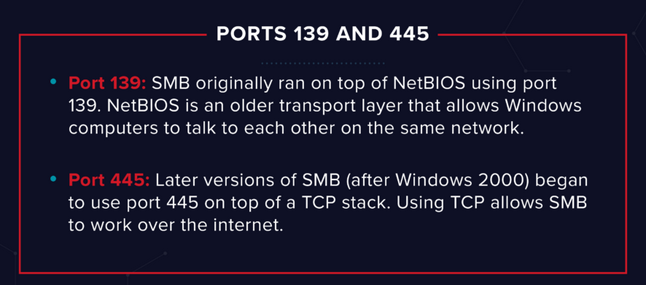
It uses TCP/IP port 445.
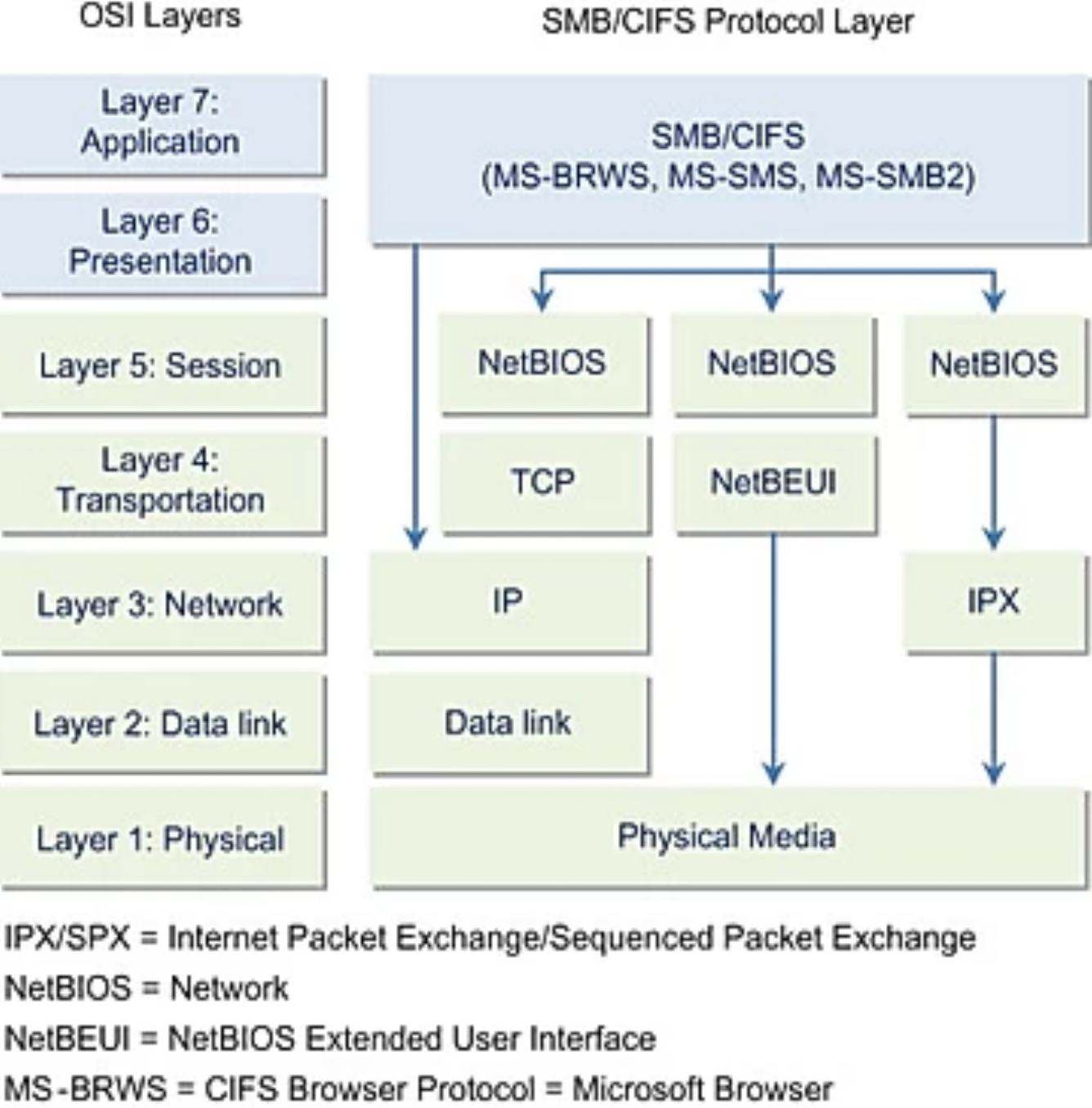
Note: CIFS(Common Internet File System) is a particular implementation of the SMB protocol, created by Microsoft. It is no longer used.
With SMB clients connect to servers via TCP/IP or NetBIOS. Once they have established a connection, the clients can send commands to access shares, read and write files and access printers.
Working
SMB uses four types of messages:
-
Session control messages: Open or close a redirector connection to a shared resource on the server. The SMB redirector packages the requests sent to remote servers in an SMB-enabled network.
-
File messages: Used by the redirector to gain access to files on the server.
-
Printer messages: Used by the redirector to send data to a print queue and get status information about the queue.
-
Message messages: Let applications exchange messages with another computer.
SMB Authentication Protocol
SMB contains two levels of security checks:
- User checks
user = client who requests to access the file
client should give their username and password for this user-level authentication check
- Share checks
share = file or folder ,directory,printer that is requested
Share-level authentication check refers to the access that is controlled by a password which is assigned to the file or share over the network.
It does not require the username to access the file.
Versions
- As the versions of SMB have increased, the performance and security level is also increased.
- SMBv1 - first version of the protocol used in Windows 2000 and Windows XP
- SMBv2 - introduced in Windows Vista and Windows Server 2008
- SMBv3 - introduced in Windows 8 and Windows Server 2012
- SMBv3.1.1 - introduced in Windows 10 Server and Windows server 2016
NetBIOS
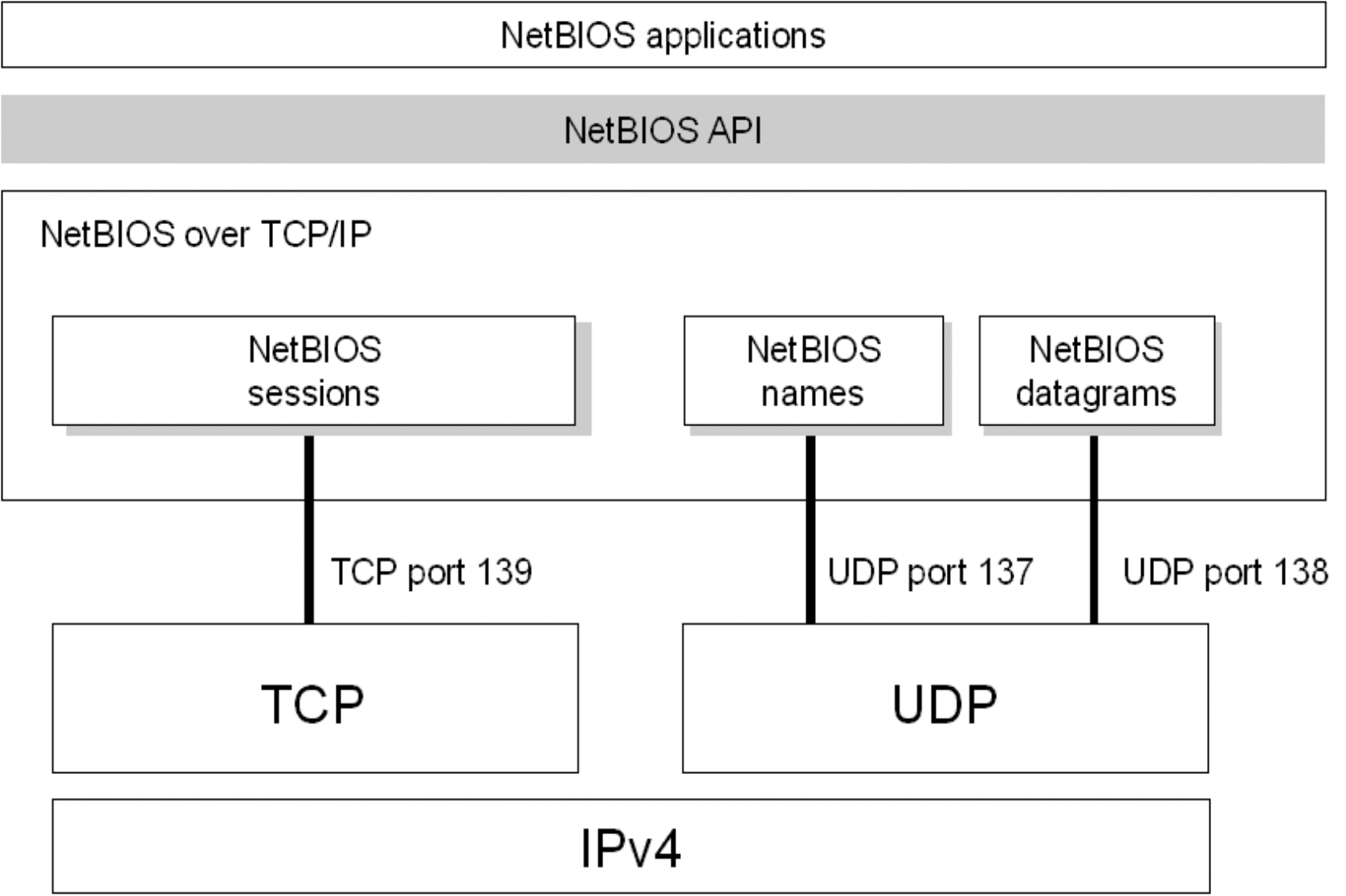
NetBIOS (Network Basic Input/Output System) allows applications and computers to communicate over a LAN for sharing files and printers.
It is often used over TCP/IP protocol (NetBT). It is not a networking protocol, it is an API.
NetBEUI (NetBios Extended User Interface)- an enhanced version of the NetBIOS protocol used by network operating systems like Windows 95 and Windows NT.
Working
NetBIOS service uses a unique 16 ASCII character string (NetBIOS Name) in order to identify the network devices over TCP/IP.
- First 15 characters - identify Devices
- 16th character - identify the service
Software applications on a NetBIOS network locate and identify each other through their NetBIOS names (provided by name service)
Two applications start a NetBIOS session when the client sends a command to "call" another client (the server) over TCP port 139. This is referred to as the session mode (since session services are used), where both sides issue "send" and "receive" commands to deliver messages in both directions. The "hang-up" command terminates a NetBIOS session.
NetBIOS also supports connectionless communications through UDP. Applications listen on UDP port 138 to receive NetBIOS datagrams. The datagram service sends and receives datagrams and broadcasts datagrams.
Datagrams - Datagram is a combination of the words data and telegram. It is a message containing data that is sent from one location to another. A datagram is similar to a packet, but does not require confirmation that it has been received.
- netbios-ns – TCP/UDP 137 # NETBIOS Name Service
- netbios-dgm – TCP/UDP 138 # NETBIOS Datagram Service
- netbios-ssn – TCP/UDP 139 # NETBIOS session service
Active Directory (AD)
It is used to manage computers and other devices on a network. It is a primary feature of Windows Server.
- microsoft-ds – TCP/UDP 445 # Directory Services for
Active Directory shares and SMB file sharing
Samba
This protocol enables Linux/UNIX systems to share resources with Windows systems as if Linux/UNIX systems are running Windows.
It uses same ports as SMB.
NT LAN Manager(NTLM)
"NT" refers to "new technology".
The NTLM protocol was the default protocol for network authentication in Windows before it was replaced with Kerberos starting Windows 2000.
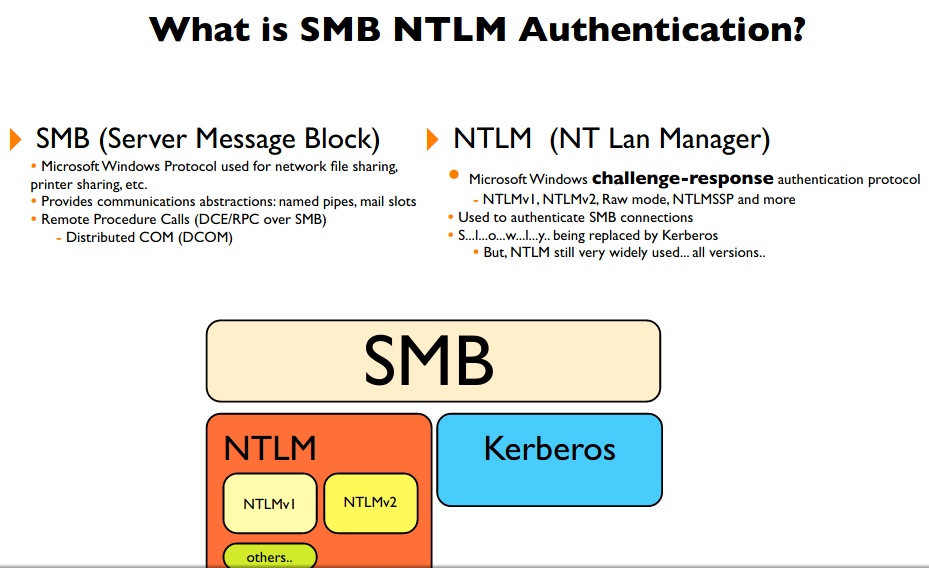
NTLM was introduced in 1993 with Windows NT 3.1 and was later improved in a second version (NTLMv2) in Windows NT 4.0.
NTLMv2 had some security improvements around strength of cryptography, but some of its flaws remained.
Working
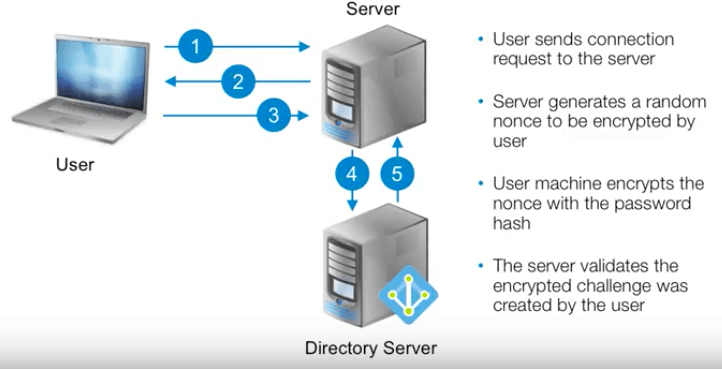
nonce - Number used no more than once
NTLM uses a challenge-response mechanism for authentication, in which clients are able to prove their identities without sending a password to the server.
It consists of three messages:
Type 1 (negotiation),
Type 2 (challenge) and
Type 3 (authentication).
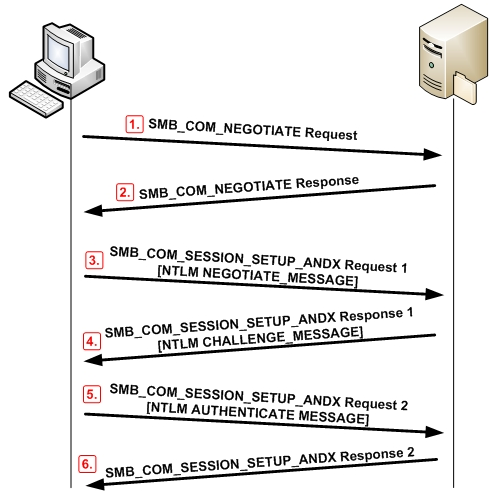
NTLM over SMB protocol is used to authenticate client's connection to SMB servers. It is easily exploitable.